Active Directory (AD) stands as a cornerstone in IT infrastructure, a critical component for managing and securing network resources in organizations of all sizes. Yet, for many IT professionals and newcomers alike, its complexities can seem daunting. This chapter aims to peel back the layers of Active Directory, transforming it from a seemingly enigmatic system into an accessible and powerful tool that enhances the efficiency and security of your network operations.
At its core, Active Directory is a directory service developed by Microsoft for Windows domain networks. It plays a pivotal role in organizing and providing access to information within an organization. Through AD, administrators can efficiently manage permissions and access to network resources, ensuring that users have the appropriate levels of access to perform their roles. From user accounts and groups to computers and other devices, AD serves as the central hub for managing identities and relationships within a networked environment.
Understanding Active Directory begins with grasping its fundamental components and structure. This chapter will guide you through the essential concepts, including domains, trees, forests, and organizational units (OUs). We will explore how AD’s hierarchical design enables scalable management and how its robust security features protect sensitive information. By the end of this chapter, you will not only demystify the complexities of Active Directory but also gain practical insights into leveraging its capabilities to streamline your system administration tasks.
Introduction to AD and its role in Windows Server infrastructure
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks, included in most Windows Server operating systems. Originally created for centralized domain management, AD has evolved to encompass a wide range of directory-based identity-related services, playing a pivotal role in Windows Server infrastructure.
What is Active Directory?
Active Directory stores and organizes information about network objects, making it easily accessible for administrators and users. It relies on a structured data store, forming a logical, hierarchical organization of directory information. This hierarchy includes domains, trees, and forests, each with varying levels of access and permissions. Domains are the basic units, housing collections of objects like users, groups, and devices. These domains can be grouped into trees, and multiple trees form a forest, which shares a common global catalog, directory schema, and configuration. Organizational Units (OUs) provide further logical grouping within a domain, facilitating easier management of resources.
Role of Active Directory in Windows Server Infrastructure
Active Directory is integral to Windows Server infrastructure due to its centralization of resource management, robust authentication and authorization services, scalability, flexibility, Group Policy management, enhanced security, directory federation services, and seamless integration with other services.
Centralized management is one of AD’s most significant contributions. It allows administrators to manage network resources such as user accounts, computers, printers, and applications from a central point. Group Policy enables administrators to enforce settings and security policies across the network efficiently. This centralized approach simplifies the management of complex network environments and enhances operational efficiency.
In terms of authentication and authorization, AD ensures that users are correctly identified and granted appropriate access to resources. This is achieved through mechanisms like user accounts and passwords, Kerberos authentication, and trust relationships between domains. These features provide a secure and reliable framework for managing access to network resources.
Scalability and flexibility are also key attributes of AD. It is designed to support environments ranging from small businesses to large enterprises, capable of handling millions of objects. AD’s delegation of authority feature allows specific administrative tasks to be assigned to different users or groups, facilitating distributed administration and reducing the burden on central IT staff.
Group Policy management is another crucial role of AD. This feature allows administrators to define and enforce configurations for operating systems, applications, and user settings across the network. By applying these configurations consistently, administrators can enhance security and productivity, ensuring that all systems comply with organizational policies.
Security is further bolstered by AD’s features such as account lockout policies, password policies, and support for smart card authentication. These features help protect against unauthorized access and ensure that security policies are consistently enforced across the network. AD’s integration with other security technologies, such as IPsec and secure LDAP, provides a comprehensive security framework.
Active Directory Federation Services (AD FS) extends AD’s capabilities beyond the organizational boundary, offering single sign-on (SSO) and identity management for cloud services and external applications. This functionality is increasingly important as organizations adopt hybrid and multi-cloud environments.
Lastly, AD’s seamless integration with other Microsoft services, including Exchange Server, SharePoint, and SQL Server, allows for unified identity and access management across different platforms and applications. This integration simplifies administration and enhances the overall efficiency of IT operations.
Active Directory is a foundational component of Windows Server infrastructure, providing a scalable, secure, and manageable framework for network resource organization and user identity management. Its central role in authentication, authorization, directory services, and integration with other technologies makes it indispensable for modern IT environments, particularly in enterprises requiring robust and flexible directory services.
Benefits of Centralized Identity and Access Management (IAM)
Centralized Identity and Access Management (IAM) offers numerous advantages to organizations by streamlining the management of user identities and access permissions. The key benefits include enhanced security, improved compliance, operational efficiency, better user experience, and cost savings. Here, we will explore these benefits in detail.
Enhanced Security
Centralized IAM provides a unified platform for managing access controls, reducing the risk of unauthorized access. By centralizing identity management, organizations can implement consistent security policies across all systems and applications. This consistency helps prevent security breaches by ensuring that access permissions are correctly assigned and regularly reviewed. Features like multi-factor authentication (MFA), single sign-on (SSO), and role-based access control (RBAC) further enhance security by adding additional layers of protection and ensuring that users have appropriate access to resources.
Improved Compliance
Compliance with regulatory requirements such as GDPR, HIPAA, and SOX is a significant concern for many organizations. Centralized IAM facilitates compliance by providing comprehensive auditing and reporting capabilities. It enables organizations to track and document who has access to what resources and when access was granted or revoked. This transparency is crucial for demonstrating compliance to regulatory authorities and for internal governance. Additionally, centralized IAM can enforce compliance policies across all systems, ensuring that all users adhere to required standards and practices.
Operational Efficiency
Managing identities and access permissions across multiple systems and applications can be complex and time-consuming. Centralized IAM simplifies these tasks by providing a single point of administration. This centralization reduces the administrative burden on IT staff, allowing them to manage user accounts, permissions, and policies more efficiently. Automated workflows for user provisioning and de-provisioning further enhance efficiency by reducing the time required to add or remove users and ensuring that access permissions are updated promptly.
Better User Experience
Centralized IAM improves the user experience by offering seamless access to resources. Single sign-on (SSO) is a critical feature that allows users to access multiple applications with a single set of credentials, reducing the need to remember multiple usernames and passwords. This convenience increases productivity by minimizing login-related delays and reducing the likelihood of password fatigue. Additionally, self-service capabilities, such as password resets and account updates, empower users to manage their accounts independently, reducing the need for IT support.
Cost Savings
By consolidating identity and access management into a centralized system, organizations can achieve significant cost savings. Centralized IAM reduces the need for multiple disparate identity management solutions, lowering licensing, maintenance, and operational costs. The efficiency gains from streamlined administration and reduced support requirements translate into lower labor costs. Additionally, the enhanced security and compliance capabilities of centralized IAM help avoid costly data breaches and regulatory fines.
In summary, centralized Identity and Access Management (IAM) offers substantial benefits, including enhanced security, improved compliance, operational efficiency, better user experience, and cost savings. By providing a unified platform for managing identities and access permissions, centralized IAM helps organizations protect their resources, streamline administration, and meet regulatory requirements. As organizations continue to grow and adopt more complex IT environments, the importance of centralized IAM will only increase, making it a critical component of modern IT infrastructure.
Core concepts: Forests, Domains, Trees, and Organizational Units (OUs)
Active Directory (AD) is a vital component of Windows Server environments, and understanding its core concepts—Forests, Domains, Trees, and Organizational Units (OUs)—is essential for novice IT professionals. These elements form the hierarchical structure of AD, allowing for organized and efficient management of network resources.
Forests
A Forest is the topmost logical container in an Active Directory structure. It represents the complete instance of AD and encompasses all other elements like Domains and Trees. A Forest provides a security boundary within which all resources share a common schema (the set of definitions for objects and their attributes) and global catalog (a directory service that holds a partial replica of every object in the forest). Think of a Forest as an overarching entity that contains everything related to AD, ensuring that all entities within it can interact and share resources if permitted.
Domains
Domains are the fundamental building blocks within a Forest. Each Domain is a collection of objects such as users, groups, and computers that share the same AD database. Domains provide a way to partition data and manage it effectively. They are also administrative boundaries; each Domain can have its own set of policies and security settings. For instance, a company might have separate Domains for different departments or geographic locations, each managed independently while still being part of the same Forest.
Trees
A Tree is a collection of one or more Domains that are connected in a hierarchical structure. Domains in a Tree share a common namespace, which means they are named in a contiguous manner. For example, if the root Domain is “example.com,” a child Domain might be “sales.example.com.” Trees allow organizations to reflect their structure in AD, with parent and child Domains representing different organizational units or geographic regions.
Organizational Units (OUs)
Organizational Units (OUs) are containers within a Domain that help organize objects like users, groups, and computers. OUs provide a way to create a logical structure within a Domain, making it easier to manage and apply policies. For example, you might have OUs for different departments like “HR,” “Finance,” and “IT.” OUs can also be nested, allowing for further subdivision within a department. This hierarchical arrangement helps in delegating administrative control and applying Group Policies. For instance, an IT admin can be given control over the “IT” OU without affecting other parts of the Domain.
Putting It All Together
Imagine Active Directory as a large company’s organizational chart. At the top is the Forest, representing the entire company. Within this company are various departments or regions, each represented by a Domain. These Domains might be grouped under broader categories or divisions, forming Trees. Within each department, there are teams or sub-departments, organized as OUs, which allow for detailed and granular management of resources and policies.
Understanding these core concepts—Forests, Domains, Trees, and OUs—should help you to grasp how Active Directory organizes and manages network resources. This hierarchical structure is designed to reflect real-world organizational needs, making it easier to manage, secure, and delegate control within an IT environment.
An Example of Core Concepts
To better understand how the core concepts of Active Directory—Forests, Domains, Trees, and Organizational Units (OUs)—fit together, let’s look at a hypothetical example involving a global company called “MyCompany Corporation.”
Forest
MyCompany Corporation has a single Active Directory Forest named “mycompany.com.” This Forest is the top-level container that encompasses all other AD elements within the organization.
Domains
Within the Forest, MyCompany Corporation has several Domains representing different geographic regions and departments. These include:
- mycompany.com: The root Domain, representing the global headquarters.
- us.mycompany.com: A child Domain representing the United States operations.
- eu.mycompany.com: A child Domain representing the European operations.
- asia.mycompany.com: A child Domain representing the Asian operations.
Each Domain has its own set of objects, such as user accounts, computers, and groups, and can be managed independently.
Trees
The Domains “us.mycompany.com,” “eu.mycompany.com,” and “asia.mycompany.com” are part of the same Tree because they share a contiguous namespace with the root Domain “mycompany.com.” This Tree structure reflects the hierarchical organization of the company’s global operations.
Organizational Units (OUs)
Within each Domain, OUs are used to further organize and manage resources. For example, within the “us.mycompany.com” Domain, MyCompany Corporation has created OUs for different departments:
- Sales
- NorthRegion
- SouthRegion
- IT
- Support
- Infrastructure
- HR
Each OU can have its own set of policies and administrative controls. For instance, the “IT” OU has sub-OUs for “Support” and “Infrastructure,” allowing specific policies and administrative tasks to be delegated to the respective teams.
Similarly, the “eu.mycompany.com” Domain might have OUs for different countries or departments:
- Germany
- Sales
- IT
- France
- Sales
- IT
Visual Representation
Here is a simplified visual representation of the MyCompany Corporation’s Active Directory structure:
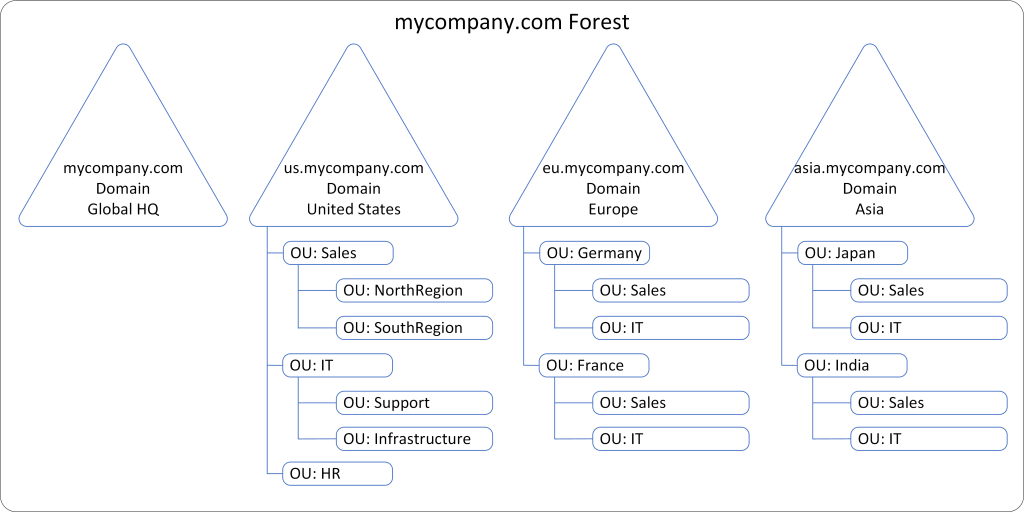
In this structure, the Forest “mycompany.com” contains all the Domains, which are organized into a single Tree with a shared namespace. Each Domain, such as “us.mycompany.com” and “eu.mycompany.com,” represents a major geographic or organizational division. Within each Domain, OUs provide a way to organize and manage resources specific to departments or regions. This hierarchical structure allows MyCompany Corporation to efficiently manage its global IT resources, enforce policies, and delegate administrative tasks appropriately.
This example illustrates how Forests, Domains, Trees, and Organizational Units work together to create an organized and manageable Active Directory environment, reflecting the real-world structure of a global organization.
Evolution of AD and Introduction to Azure Active Directory (Azure AD)
Active Directory, a cornerstone of contemporary IT infrastructure, has evolved significantly since its inception. Its journey reflects the dynamic nature of technology and the growing complexity of network management.
First, a Little History
Prior to Active Directory, Windows NT introduced domains as a means of managing groups of computers under a primary domain controller. While a step forward, NT domains had inherent limitations. Their flat structure made administration cumbersome in large organizations, and scalability was a persistent issue. Moreover, the functionality offered by NT domains was relatively basic, primarily focused on authentication and authorization.
With the release of Windows 2000 Server, Active Directory marked a transformative shift in network management. Built upon the foundation of NT domains, it introduced a hierarchical structure that facilitated better organization and delegation of administrative responsibilities. A key innovation was multi-master replication, which ensured high availability and fault tolerance by replicating changes across multiple domain controllers. Additionally, Active Directory adopted LDAP compatibility, fostering integration with other directory services. Its rich object model extended management capabilities beyond users and computers to encompass a wider range of network resources.
Subsequent Windows Server releases have continuously refined Active Directory. Windows Server 2003 introduced Group Policy for streamlined configuration management and strengthened security measures. Windows Server 2008 prioritized virtualization support, PowerShell integration, and performance enhancements. Cloud integration, federation services, and advanced security features like Device Health Attestation were focal points in Windows Server 2012. Building on this foundation, Windows Server 2016 emphasized identity and access management, integrating Azure AD, introducing Windows Hello for Business, and bolstering security with Credential Guard. The trend continued with Windows Server 2019, which furthered hybrid environment support, security, and performance through features like Windows Defender Advanced Threat Protection integration. Most recently, Windows Server 2022 has refined Azure AD integration, simplified hybrid identity management, and fortified security with Protected Users.
Into the Modern Times
Today, Active Directory remains indispensable in many organizations’ IT infrastructures, but its role has expanded considerably. It seamlessly integrates with cloud-based services like Azure AD, creating hybrid identity and access management solutions. As a critical component of an organization’s security framework, it provides essential authentication, authorization, and threat protection. Moreover, tools like PowerShell automate management tasks, reducing administrative burdens. Microsoft’s ongoing commitment to Active Directory ensures its adaptability to emerging technologies and security challenges, solidifying its position as a vital platform for managing identities, devices, and applications across on-premises and cloud environments.
